Tokenization vs Encryption: What’s the Difference?
Tokenization and encryption are often mentioned together because they both disguise sensitive card data, however, they are not interchangeable terms. Today, customers expect the convenience of automatic and card-on-file payments along with the peace of mind that their sensitive card data won’t get lost or stolen. Much of this is possible because of tokenization and encryption.
Tokenization
Tokenization is a replacement technique. Put simply, the tokenized information uses a stand-in for all the transaction tasks. The payment gateway provider holds the sensitive data in its token vault and will issue a completely different number string that can be used for card-based transactions. This number string can only be exchanged for the real credit card number once the token is sent to the acquirer (for example, Clearent), at which point the transaction can be authorized. This protects businesses from compromising cardholder data because they never see or store any data of value. There is no code, passkey or algorithm that can convert the token back to real data. It can only be replaced by the original credit card information by the bank or processor. A real-world example of a token is a personalized transit pass that stands in for a cash fare and is useless to any other person because of its unique features, such as an embedded photo ID. A transit pass is a token, representing the money already held in the transit company’s vault. Tokenization allows merchants to offer customer-friendly services such as storing cards on file and processing recurring payments. This makes it an ideal solution for subscription-based or membership-based businesses. Tokenization is also a good technology for online businesses who want to store customer information for future purchases. Tokenization eliminates Payment Card Industry Payment Application Data Security Standard (PCI PA DSS) scope for software vendors because it allows them to only store non-sensitive card data. Businesses can also reduce their obligations under the Payment Card Industry Data Security Standard(PCI DSS) when they use tokenization.
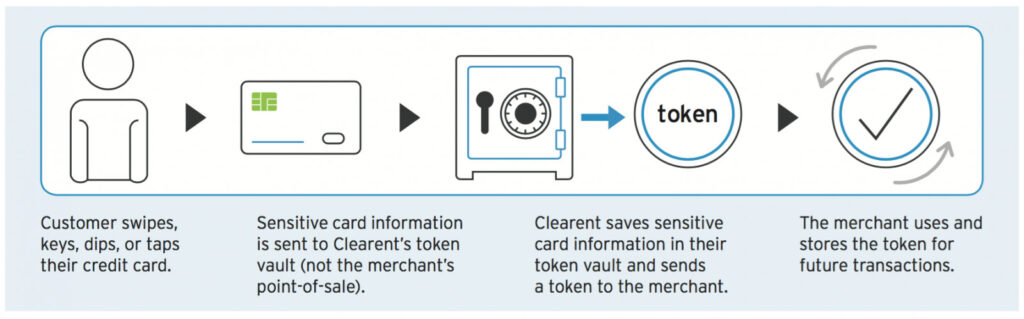
Encryption
In contrast to tokenization, encryption disguises sensitive card data by turning it into unreadable code. Before leaving one computer or card reader and embarking on a trip across a network, card data is obscured using a coding system that replaces each number, letter or space for a different one using a sophisticated encryption algorithm. This new encoded version of the data must be decrypted at the other end of its journey using the key or password. Encryption comes in a variety of styles and has been used for centuries with ever-increasing sophistication and complexity. Without the passkey or encryption key, a thief would have to spend inordinate amounts of energy and time to decode an encrypted message. However, the fact that the original message or account number is still present, even heavily disguised, means that an organization must ensure the entire process used to store and transmit the data complies fully with PCI DSS requirements. Encryption only reduces PCI scope when the solution is validated by the PCI Data Security Council. For example, PCI-Validated Point-To-Point Encryption (P2PE) goes through a strict and rigorous vetting process by the PCI Data Security Council. Therefore, businesses using a PCI-validated encryption solution qualify for a shorter PCI self-assessment questionnaire.
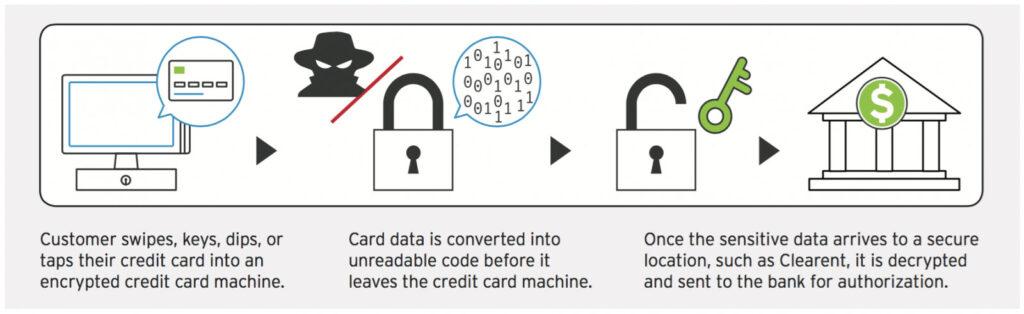
Encryption ciphers card data as soon as it is swiped/dipped/keyed into an encrypted credit card machine. This is a great tool for businesses who need to accept cards in person, such as retail stores.
Side-by-Side Comparison
| Tokenization | Encryption | |
|---|---|---|
| How it works | Replaces sensitive data with a randomly generated code, also known as a token | Disguises sensitive data by turning it into unreadable code using an encryption algorithm and key |
| What kind of data does it support | Structured data, such as payment card or social security numbers | Structured data, such as payment card numbers, and unstructured data, such as entire files and emails |
| Use cases | 1. Card-on-file payments 2. Recurring payments 3. E-commerce transactions 4. Storing customer data across multiple locations | 1. In-person transactions 2. Payments over the phone |
| Security strength | HIGH – Sensitive data never leaves the organization | HIGH – Sensitive data leaves the organization in encrypted form. PCI-validated (P2PE) goes through a strict vetting process by the PCI Security Standards Council |
| PCI implications | 1. Eliminates PCI PA DSS scope for software vendors 2. Reduces PCI scope for businesses | 1. Eliminates PCI PA DSS scope for software vendors 2. PCI-validated solutions reduce PCI SAQ scope for businesses |
What Should Your Business Use: Tokenization or Encryption?
The answer is both, whenever possible. Tokenization is vital for use with card-on-file and recurring payments, both online and in store. It is also essential for businesses using multiple locations or franchises. Encryption is essential for card-present payments.
How Do These Technologies Reduce PCI Scope?
P2PE removes software vendors from PCI PA DSS scope. PCI-validated P2PE reduces businesses’ PCI scope and allows them to take a much shorter PCI questionnaire.
Article by Clearent by Xplor
First published: March 17 2023
Last updated: March 28 2024

